SonicWALL Hidden Features Access799
Pages:
1

|
LiquidLayer private msg quote post Address this user | |
| See Source Post: http://www.beacontechnologies.com/blog/2016/03/sonicwall-hidden-features-and-diagnostic-routines/ SonicWALL Hidden Features and Configuration Options  Earlier I stumbled across a hidden set of features and settings in a TZ215 by going to /diag.html and figured Id share this with everyone in case you were unaware of it as I was. It appears to be available in all of the TZ series devices, the SOHO, and likely others. On the main page you will see the following disclaimer.  Under Internal Settings there are quite a few settings and options. Some more useful than others. For me the option I needed was “Disable Port Scan Detection” under the Firewall section. Below is a rough list of some of the options. Keep in mind these options are undocumented, unsupported, and it is suggested to only make changes to these values if instructed by Dell Technical Support. Enjoy! 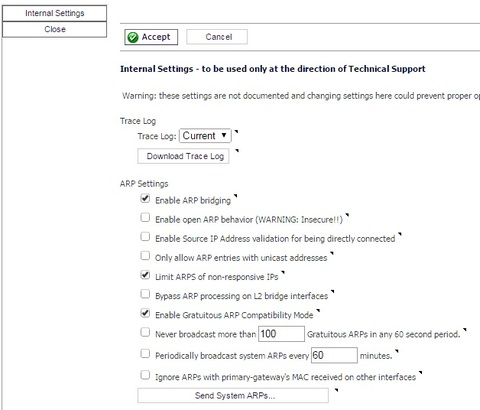 Trace Log: Trace Log: [Current /] [Download Trace Log] [Clear Trace Log] ARP Settings: Enable ARP bridging Enable open ARP behavior (WARNING: Insecure!!) Enable Source IP Address validation for being directly connected Only allow ARP entries with unicast addresses Limit ARPS of non-responsive IPs Bypass ARP processing on L2 bridge interfaces Enable Gratuitous ARP Compatibility Mode Never broadcast more than 100 Gratuitous ARPs in any 60 second period. Periodically broadcast system ARPs every 60 minutes. Ignore ARPs with primary-gateway’s MAC received on other interfaces [Send System ARPs...] Routing and Network Settings: Flush flows on alternate path when normal route path is enabled (affects existing connections) Update route version when route is enabled/disabled (affects existing connections) Enable TCP packet option tagging Fix/ignore malformed TCP headers Enable TCP sequence number randomization Perform SYN validation when not operating in strict TCP compliance mode [Clear OSPF Process] Clear DF (Don’t Fragment) Bit Allow first fragment of size lesser than 68 bytes Enable ICMP Redirect on DMZ zone Disable learning-bridge filtering on L2 bridge interfaces Never add static default routes to the NSM route database Enable stack traffic sending by DP core DHCP Settings: Enable DHCP Server Network Pre-Discovery DHCP Server Conflict Detect Period: 300 Seconds Number of DHCP resources to discover: 10 Timeout for conflicted resource to be rechecked: 1800 Seconds Timeout for available resource to be rechecked: 600 Seconds [Save DHCP Leases To Flash] Send DHCPNAK if the ‘requested IP address’ is on the wrong network Time interval of DHCP lease database to be refreshed: 600 Seconds Number of DHCP leases in database to be refreshed: 10 Aggressively recycle expired DHCP leases in advance VoIP Settings: Maximum ‘public’ VoIP Endpoints: 2048 H.323 Force Odd Media Control Port Auto-add SIP endpoints Transform SIP URIs to have an explicit port Permit B2BUA to bind established calls together SIP connection refresh interval (seconds): 40 Flush active media for SIP INVITEs without SDP Flush unused media for SIP INVITEs without SDP [Reset SIP Databases] VPN Settings: Do not adjust TCP MSS option for VPN traffic Use interoperable IKE DH exchange Fragment VPN packets after applying ESP Use SPI/CPI parameter index for IPsec/IPcomp passthru connections Accept Reserved ID Type in Quick Mode. Trust Built-in CA certificates for IKE authentication and Local certificate import. Enable Compatibility with Android 4.0 Client. Encryption Settings: Enable Hardware Encryption Disable SSLv3 Disable TLSv1 DP stack Settings: Enable DP stack processing Firewall Settings: FTP bounce attack protection Allow orphan data connections Allow TCP/UDP packet with source port being zero to pass through firewall FTP protocol anomaly attack protection IP Spoof checking Disable Port Scan Detection Trace connections to TCP port: 0 Include TCP data connections in traces Enable Tracking Bandwidth Usage for default traffic Enable to bandwidth manage WAN to WAN traffic Decrease connection count immediately after TCP connection close Protect against TCP State Manipulation DoS Disable CSRF Token Validation Disable Secure Session ID Cookie [Flush Connections] Deschedule Packet Count: Refresh sub-domains of wildcard FQDN address objects Security Services Settings: Apply IPS Signatures Bidirectionally Enable IP fragment reassembly in DPI Extra dev debug info Disable TCP expected sequence adjustment in DPI Disable App-Firewall SMTP CHUNKING modification Disable Gateway AV POP3 Auto Deletion Disable Gateway AV POP3 UIDL Rewriting Disable Gateway AV SMB read/write ordering enforcement Log Virus URI. Do not apply signatures containing file offset qualifiers that trigger on TCP Streams with unidentified protocols. Minimum HTTP header length (0 to disable): 0 Enable incremental updates to IDP, GAV and SPY signature databases. Enable enforcement of a limit on maximum allowed advertised TCP window with any DPI-based service enabled. 256 Set a limit on maximum allowed advertised TCP window with any DPI-based service enabled (KBytes). Disable signature database reload. 1500 Threshold above which size limits are enforced on Regex Automaton. 3000 Maximum allowed size for Regex Automaton. Limit IPS CFT scan. Enforce Host Tag Search for CFS [Reset AV Info] [Reset Client CF Enforcement Info] [Reset Client CF Enforcement Cache] [Reset Licenses & Security Services Info] [Reset HTTP Clientless Notification Cache] [Reset Cloud AV Cache] DPI-SSL settings: Rewritten certificate SN modifier: Client spoofed certificate caching: Remove TCP timestamp option: Drop SSL packets when memory low: Allow SSL without proxy when connection limit exceeded: Disable Endpoint TCP Window Setup: Disable Server Facing Session Reuse: Block connections to sites with untrusted certificates: 512 Max stream offset to check for SSL client-hello resemblance: TCP window multiplier (N * 64k): Override max proxied SSL connections: Disable SSLv3 client connections in DPI-SSL: SSL Version: Cipher Methods High Availability Settings: Enable Network Monitor probing on Idle unit HA Failover when Packet Pool is Low on Active Unit Suppress Alarm on HA Transition to Active Always restart HA backup for watchdog task Send gratuitous ARP to DMZ or LAN on transparent mode while HA failover Maximum number of gratuitous ARP of transparent mode per interface while HA failover: 256 Maximum number of gratuitous ARP while HA failover: 1 Send Syslog messages from both HA units with unique serial numbers PPPOE Settings: Allow LCP requests to PPPOE Server Log LCP Echo Requests and Replies between client and server Enable PPPoE End-Of-List Tag PPPOE Netmask: 255.255.255.0 Dial-Up Settings: Display dialup status on console PPPDU Max Configuration Failures: 9 [Restart Dial-Up Devices] One-Touch Configuration Helpers [DPI and Stateful Firewall Security] Preview applicable changes [Stateful Firewall Security] Preview applicable changes Management Settings: Use Standby Management SA Allow SGMS to preempt a logged in administrator Prioritize the following selected traffic types below to be highest and above all other traffic types: ICMP SNMP HTTPS User Authentication Settings: Post authentication user redirect URL: [ ] Log an audit trail of all SSO attempts in the event log (X) in the event log ( ) in memory to download as ssoAuthLog.wri, max. buffer size: 64 KBytes. - When buffer is full: (X) stop ( ) wrap. Download ssoAuthLog.wri Download and reset ssoAuthLog.wri For user IP addreses: [All /] Include SSO polling Include SSO bypass Include additional non-initiation of SSO Try to negotiate SSO agent protocol to version: 5 (default protocol version is 5) [Logout All users] Diagnostics Settings: Disable SonicSetup/Setup tool Server Trace message level: [Warning /] For diagnostic testing purposes, auto-restart system every 60 minutes. Secured www.mysonicwall.com crash analysis Watchdog Settings: Do not restart for watchdog task Restart quickly after an exception Restart when packet pool is low IPHelper Settings: Enable no source port matching for replies from DHCP servers. Disable Reverse Path check for Source IP. Disable ingress egress check. Wireless Settings: Wireless Advanced Settings Set Local Bit for Virtual Access Point BSSID MAC Address Allow same Virtual Access Point groups to be used for dual radios Supported SonicPoint Type: [All /] SonicPoint-N System Self Maintenance: [Weekly (3:00AM Every Sunday) /] Legacy SonicPoint A/B/G and SonicPoint-G Only Management Enforcement [Update All SonicPoint's Firmware] SonicPoint KeepAlive Enforcement SonicPoint Provisioning Protocol TCP Window Size: 1400 Use Default TCP Window Size For SonicPointN Provisioning Protocol SonicPointN Provisioning Protocol TCP MSS Setting: (X) Use Default Value. ( ) Customized TCP MSS: 1460 bytes. Prefer SonicPointN 2.4GHz Auto Channel Selection to be 1, 6 and 11 only SonicPointN SSH Management Enable Enable SonicPoint (N) IP address retaining SonicPointN Logging Enable Erase SonicPoint Crash Log generated by previous firmware image when SonicPoint image is updated SonicPoint-Ni/Ne Noise Sensitivity Level: (The higher noise sensitivity level should be selected when RF environment is getting noiser) [Medium /] SonicPointN Reboot When Noise Safe Mode Detected Use SNAP packet between SonicPoint / SonicPointN and Gateway Send Need Fragment ICMP packet to SonicPoint / SonicPointN client Enable intra-WLAN Zone communication for bonjour packet WLAN DHCP lease / ARP delivery success rate enhancement Wireless Guest Services Redirect Interval: 15 Seconds Legacy WiFiSec Enforcement support Do not apply WiFi security enforcement on reply traffic from WLAN to any other zone Enable WLAN traffic DP core processing capability Enable intra-WLAN Zone communication for broadcast packet Enable local wireless zone traffic to bypass gateway firewalling Tooltip Settings: Enable tooltip with no descriptions Preferences Conversion: Preference Processor Server: convert.global.sonicwall.com Site Relative Directory: /popup Enable checking when importing settings Anti-Spam Service: Disable SYN Flood Protection for Anti-Spam-related connections Use GRID IP reputation check only Disable GRID IP reputation checking for Outbound SMTP connections Do NOT disable custom user email policies when Anti-spam is enabled Allow Limited Admin users to configure Anti-Spam Service. Bypass SHLO Check when Junk Store is unavailable (while Email Security is operational). Do NOT verify incoming SHLO Marked as replay if incoming SHLO time stamp is more than: 3600 secs [Clear Statistics] [Reset GRID Name Cache] [Delete Policies and Objects] CASS Cloud Service Address: [Resolve Automatically /] Email System Detection: Enable Email System Detection TZ Default Port Assignment: TZ Basic (LAN/WAN) Mode Remote Assistance: Enable Remote Assistance SSLVPN Settings: NetExtender(for Windows) Version: [ ] Hide Remote EPC feature WAN Acceleration Settings: Enable checking of connection responses by remote WAN Acceleration device Temporarily bypass TCP Acceleration for failed proxied connections (minutes): 15 Temporarily bypass TCP Acceleration for short-lived proxied connections (minutes): 60 Skip TCP Acceleration for stateful control channels (but accelerate data channels) Enable Transparent CIFS acceleration Enable WXA Web Cache Redirection [Zero debug stats] [Show debug stats] [Open WXA Internal Settings Page] [SSH to WXA appliance] Backend Server Communication: Prevent communication with DELL Backend servers Server Connection Timeout (sec): 30 Log Settings: Exempt unfiltered events from global, category-level and group-level changes [Restore Unfiltered Event Settings] Main Log Process Reschedule Interval: 100 Log Entries SMTP Read Timeout (sec): 10 IPv6 Settings: Enable enforcement of IPv6 Ready Logo requirement ICMP Settings: Enable enforcement of Dropping Unreachable ICMP packet Enable enforcement of Dropping Time Exceed ICMP packet Debug Option: Disable Pkt Monitor Application Detection See Source Post: http://www.beacontechnologies.com/blog/2016/03/sonicwall-hidden-features-and-diagnostic-routines/ |
||
| Post 1 • IP flag post | ||
Pages:
1
