SonicWall SonicPoint Install Tips 101684
Pages:
1

|
LiquidLayer private msg quote post Address this user | |
| Here are some resources for setting up SonicPoints with a SonicWall Firewall. The Firewall will become the Wireless Controller for all Sonic Points (Access Points) inside of the trusted subnet. 1st off - Follow the SonicPoint Quick Startup Guide http://www.sonicwall.com/downloads/SonicPoint_N_GSG_web.pdf If you want to allow the Wireless Clients to communicate to Wired Hosts, without using Layer2 Bridge Mode: https://support.software.dell.com/kb/sw8334 Same process here / but bigger screen shots, perhaps more cooler as well, big arrows, nice walk though http://briandagan.com/fix-configuring-sonicpoint-aps-on-a-sonicwall More advanced stuff - prior to 5.9 layer 2 was most common, but 5.9 add the ability for Layer 3 deployments SonicOS 5.9 SonicPoint Layer 3 Management Guide: http://us-downloads.quest.com/Repository/support.quest.com/SonicWALL%20TZ%20Series/105/Documentation/SonicOS_5.9_SonicPoint_Layer_3_Management_Guide.pdf Here is more resources we found: There are many factors that affect performance through any wireless access point, and the SonicWALL SonicPoint is no exception. Understanding your environment and preparation is key to getting the best out of your equipment. Any compromises along the way will make a difference in the end. There a a number of resources from SonicWALL that you should be aware of first and these are: SonicWALL SonicPoint Series Datasheet (ACe/ACi & N2) SonicWALL Clean Wireless Datasheet (NDR/Ni & Ne) Getting Started Guide - SonicWALL SonicPoint ACe Getting Started Guide - SonicWALL SonicPoint Aci Getting Started Guide - SonicWALL SonicPoint N2 Getting Started Guide - SonicWALL SonicPoint N Dual-Radio Getting Started Guide - SonicWALL SonicPoint-Ne / SonicPoint-Ni SonicWALL SonicPoint Deployment Best Practices Guide (older guide) Liquid Layer Networks | Performance Cloud Web Hosting http://www.LiquidLayer.net ParagonHost Networks | Web Hosting since 2000 http://www.ParagonHost.net |
||
| Post 1 • IP flag post | ||

|
LiquidLayer private msg quote post Address this user | |
| http://www.brandontek.com/networking/solution-to-your-sonicpoint-wlan-woes/ Sonic Points to need connectivity "directly" to the allocated WLAN Interface The above URL explains this well and using VLAN's to resolve if terminating on a LAN segment that is NOT directly connected to the allocated WLAN interface on the SonicWall Or As noted above via BrianDagan.com The solution to "mix" SonicPoints and Wired hosts on the same physical lan segment. BrianDagan.com solution will Bridge our WLAN interface with X0 , so you just need one uplink cable to your network switch. http://briandagan.com/fix-configuring-sonicpoint-aps-on-a-sonicwall SonicWall's Tech Note - notes: How to allow TCP communications between Wireless (Authenticated to SonicPoints) and Wired Hosts connected to the same network WITHOUT using Layer2 Bridge Mode. (SW8334) https://support.software.dell.com/kb/sw8334 Title UTM - Wireless: How to allow TCP communications between Wireless (Authenticated to SonicPoints) and Wired Hosts connected to the same network without using Layer2 bridge Mode. Resolution Article Applies To: SonicWALL Security Appliance Platforms: Gen5: NSA E8500, NSA E7500, NSA E6500, NSA E5500, NSA 5000, NSA 4500, NSA 3500, NSA 2400, NSA 2400MX, NSA 240 Gen5 TZ Series: TZ 100, TZ 100 Wireless, TZ 200, TZ 200 W, TZ 210, TZ 210 Wireless SonicPoints: SonicPoint N, Ni/Ne*, SonicPoint a/b/g *(SonicPoints Ni/Ne require SonicOS 5.6.0.3-40o and higher) Firmware/Software Version: SonicOS 5.5.0.0 and above Feature: How to allow TCP communications between Wireless hosts (Authenticated to SonicPoints) and Wired Hosts connected to the same network without using Layer2 bridge Mode. Procedure: 1. Configure any unused interface with a Zone of security type "Wireless" where SonicPoints and Wired Hosts will be connected to. (You can also create a custom Zone, but the Security type of the Zone should be "Wireless" In this case, both Wireless and Wired Hosts are connected to the same 192.168.56.0/24 network. 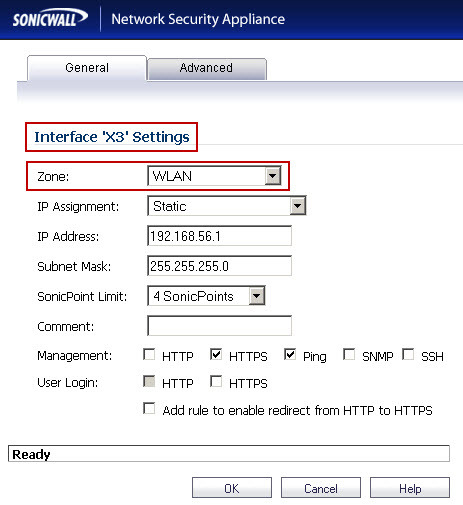 2. Go to the diagnostic page, select "Internal Settings" and under "Wireless Settings", enable "Enable local wireless Zone traffic to bypass gateway firewalling" checkbox and select "Accept" on the top.  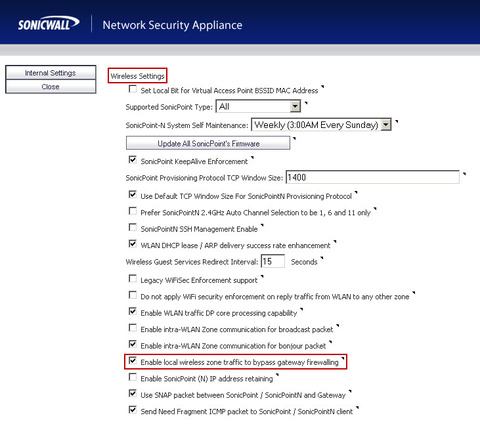 3. Go to Network -> Zones and edit the properties of the Zone that is used in Step1: Enable "Allow Interface Trust"; Disable "Only allow traffic generated by a SonicPoint/ SonicPoint N"; Enable "Enable local wireless Zone traffic to bypass gateway firewalling" 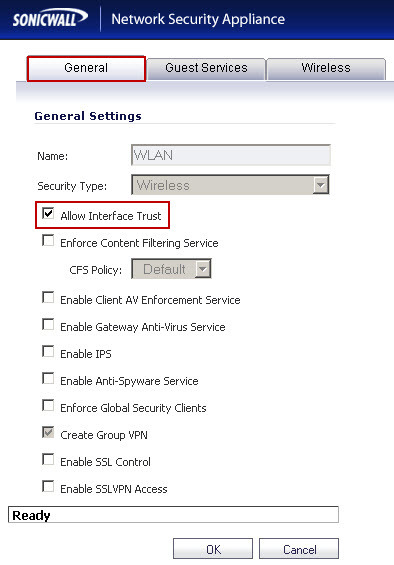 https://www.fuzeqna.com/sonicwallkb/wf/uploadfiles/Image/KBID8334-WLANZoneWireless.jpg 4. Re-provision the SonicPoint(s) for the changes to take effect How to Test: Choose a Wired host and a Wireless host on 192.168.56.0/24 network and test any TCP connectivity - For Example, RDP Access Liquid Layer Networks | Performance Cloud Web Hosting http://www.LiquidLayer.net ParagonHost Networks | Web Hosting since 2000 http://www.ParagonHost.net |
||
| Post 2 • IP flag post | ||

|
LiquidLayer private msg quote post Address this user | |
| *** Daisy Chaining SonicPoints / NOT Recommended ... However since there is some dialog within documentation that was hard as heck to find - Here is some notes about using this method along with a couple of links to Tech Documents: There is VERY little info anywhere on this …. However , couple of things / as noted under the Important note inside of the document is that ACe and ACi which is the current available SonicPoint “only” support two SonicPoints / one additional connected via the LAN2 interface on the SonicPoint … or as noted and as you stated / you can loop up to 4 access points but will encounter degraded throughput. However this “does not” increase the Loop Limit of Ethernet ( max 328 feet ) https://documents.software.dell.com/sonicos/6.2/administration-guide/sonicpoint/understanding-sonicpoints/about-sonicpoints/sonicpoint-capabilities/sonicpoint-capabilities?ParentProduct=847 LAN 2 does “not “ support POE as noted here: https://support.software.dell.com/kb/sw13630 Meaning that there will need to be a POE Injector brick installed on the wire that is terminated from LAN2 off the SonicPoint. Please note that “Daisy Chaining” SonicPoints as noted in the document is really for convenience and to “save” on interface switch ports. It will not increase the “data” loop limit of Ethernet 328 Feet. It will not act as a Ethernet Loop Distance booster. Best way to deal with Ethernet Limit’s is multiple network switch’s deployed with fiber uplinks between them. *** The Net Result of a daisy chained SonicPoint Environment beyond “one hop” for ACi or Ace is reduced throughput *** Net Result of attempting to support a daisy chained SonicPoint Environment beyond “the 328 foot loop limit of Ethernet” is loss of communication from SonicPoints beyond the Ethernet limit. |
||
| Post 3 • IP flag post | ||

|
LiquidLayer private msg quote post Address this user | |
| How far can I run Cat 5e or Cat 6? http://fourpair.blogspot.com/2005/03/how-far-can-i-run-cat-5e-or-cat-6.html |
||
| Post 4 • IP flag post | ||
Pages:
1
