The Changing DDoS Landscape a Perspective631
Pages:
1

|
LiquidLayer private msg quote post Address this user | |
| How Prepared are You for the Changing DDoS Landscape? WHIR Service Provider Q&A via Incapsula Blog By Tim Matthews / See source above Nicole: You touched on this a little bit during your presentation, Tim, but I think this is a good question so I’ll ask it anyway. It comes from Philip. He says, from time to time, we see the nature of DDoS change. One month it’s NTP, the next DNS amplification, etc. Do you observe similar trends, any explanation? Tim: Yes. It’s a really good question. The short answer is that criminals will try whatever they can to get in. I mentioned that one attack that lasted 38 days. We saw almost every known type of DDoS attack against that customer. You can think of it, it’s a crude analogy, but breaking into a building. You try the front door, you try the back door, you try the window, try the garage. We see the criminals find a lot of different things. We also often see a particular, what we suspect to be a single criminal group, who might have a preferred technique and they keep hitting a lot of sites with the same technique. We also see hacktivists – Anonymous has been recently talking about hitting various entities with DDoS attacks – who might have a preferred method. For example, if you’re going to hit a bank, you know they’ve got defenses in place. You know it’s going to take a lot of volume. You might see more of a volumetric attack. The DDoS trends report will give you more details on what we’re seeing. That was actually distilled from what we saw in the last year. I fully expect to see novel, new DDoS attacks come up in the next report. One that we saw recently was quite ingenious. Somebody put malware inside the image tags on a video sharing site. Everyone that went to that site and looked at the page would download all the little images next to the comments and then would become infected and then become part of a big DDoS botnet. We’re always amazed at the innovation shown by the DDoS attackers. We expect to see a lot of change to continue for the next several years. Nicole: The next question is, what’s the most common misconception of DDoS or mitigating DDoS attacks? Tim: I think the most common misconception, which is maybe just an outdated notion, is that all you need to do is have overprovisioning of bandwidth and you’re good. I think it’s a bad idea because you probably don’t have enough bandwidth and you’re not keeping up with the size of attacks. Even if you are, you’re totally wide open to the application-layer attacks. Having more bandwidth is not going to protect you from someone going after you or your customer’s web apps. That’s probably the biggest one. Nicole: I’ve got another attendee here asking about CloudFlare DDoS protection. The question is, I guess, just asking you about CloudFlare DDoS protection and, I guess, what you think of it. Tim: Sure, they’re our competitor. You’ll know right away that I’m biased. Since you asked the question, they’re a worthy competitor of ours. We do believe in just talking about DDoS alone, that our ability to deal with application-layer attacks is more sophisticated. We have a lot of engineering background in our company that comes at what I call web application firewalls, or WAFs. Our bot identification, we believe, is more sophisticated and will cause fewer false positives. We also believe our network is a bit more robust. I think that you’ll find, for those who are interested in BGP protection, which I mentioned, which is the direct IP or direct-to-origin attack, that our services is much more advanced. What I’d say is we both offer free trials. I wouldn’t take it from me. Try it for yourself and see what you think. Nicole: It seems like a lot of people think most attackers are in Russia or China. Is that accurate or is it spoof traffic for the most part? Tim: First of all, we know for sure that there are criminal syndicates operating out of Russia. This is not something we discovered. You can go and look online to find out about it. I believe that people are taking advantage of that and routing through Russia in particular and also through China. I think it’s somewhat of a misconception. If I can read in to the question a bit, if you only block traffic from Russia and China and think that you’re safe, you are not. There are criminals all over the world, not just in cybercrime, but every kind of crime, and a lot of the guys who are going through Russia or China will just mask probably their tracks or mask their true IP locations. 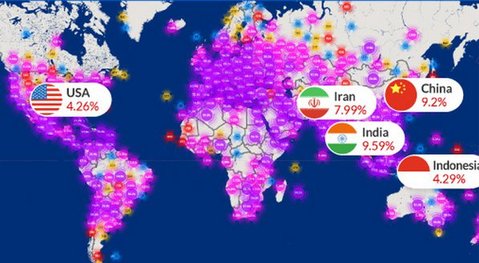 IP map of DDoS botnet attacks. Source:Incapsula's DDoS Threat Landscape Report Nicole: Has there been a recent increase in attacks in the last two weeks? Tim: I can’t say that we saw a specific spike in attacks in the last two weeks. However, that person may be referring to the Anonymous threats, against financial institutions. They’ve threatened a few government entities as well. Sometimes what happens is you get high-profile hacktivists going after high-profile targets and it gets covered in the press, and people presume that that just means there’s an uptake but sadly there is cybercrime happening every day, probably right now. DDoS attacks are happening all the time. We have seen a year-over-year volume increase. I don’t know that we saw the actual number of attacks. I have to go back and look at that and see if we have any information on the sheer number. I would presume there are more because it’s, like I said in the beginning, it’s cheaper and easier than ever for attackers. I would expect there would be more year-over-year. I don’t have data to back that up. Nicole: The next question is, where are your scrubbers located? Tim: Good question. We have 21 PoPs around the world, going on 30. Instead of listing all 21 right now, if you go to our homepage, you can see a map. Every PoP of ours is effectively a scrubbing center. We distribute any cache or traffic across the globe. Think of it as right now, 21 scrubbing centers going on 30. We’ve got them in North America, Europe, South America, and Asia. Nicole: Is there a specific service or industry that gets targeted more? Tim: It’s hard to say exactly on a vertical, like a typical SIC code or industry code, but I’ll tell you, off the top of my head, some of the top targets that we see. E-commerce is a big one.SaaS is a big one. Any kind of financial exchange especially, even these days, bitcoin exchanges get hit a lot. Gaming sites, both gambling as well as video game or multiplayer game, those are all really common. That being said, we’ve seen fast food chains. We’ve seen manufacturing companies. We see hacktivism more targeted against governments, banks but even, for example, we had a fast food chain where the CEO made a comment about a social policy that was controversial and they got targeted. In that case, it depends on the position of your company or the kinds of things your CEO says. We didn’t talk a lot about this but a very common tactic is to send ransom notes. The game is you rent a botnet for $500 and then you send out 20 ransom notes for $500, and you think that maybe you might get two or three people to pay you. In those cases, it’s simply typically after geographic regions or IP ranges indiscriminately. There’s no real contemplation of the industries. Nicole: The next question is related to price. How is DDoS priced? How does a service provider know how much protection they need? Tim:Good questions. The simplest example or the simplest way to describe it is a DDoS protection from a service provider like us is typically priced per month per site. There’s also a bandwidth addition if you feel you might need extra bandwidth protection. Just to give you a sense, an individual blogger like me could get a free plan or might be paying $50 a month. Enough for a blog. A small business might be paying on the order of $300 a month, and then like I said earlier, some of the big multinationals with hundreds of sites and big bandwidth concerns, might be paying on the order of, I’m trying to do some quick math in my head here, on the order of $25,000 a month. It can scale quite a bit. Really, it’s very flexible depending on the needs of the customers. How you know how much you need, there’s how many sites is a pretty obvious one. You can contemplate how much traffic is currently running through your site. We could advise you on the types of attacks that we see and how much protection you might need. We do that with our customers. If you wanted to see our pricing, it’s on our website at Incapsula.com. You can see literally what the plans are and what you get. It’s a pretty broad range and it depends mostly on the number of sites and then bandwidth. Nicole: The next question is related. It’s how much can I charge my customers for DDoS? Tim: Good question. I would basically just go back to my previous answer. That’s the market rate for DDoS protection, what I just summarized. You wouldn’t want to charge more than that. The way we particularly work with resellers is like any other reseller that we sell to them at a discount and then they resell to their customers at a market rate. That’s the simplest answer. If you go to the pricing page I mentioned, and you look at what we charge customers for our online plans, where no sales person is involved, just a person using a credit card. Those are the current market rates for DDoS that you would look to charge your customers. Nicole: The next question, is it often the case that a hosting company protects itself and resells DDoS to its customers? Tim: The answer is yes. It’s quite common that the company will protect itself and resell to customers. I think the scenario I gave earlier is very common where the company might, for example, buy a certain level of protection for itself and they might actually use our BGP solution which might be something that they switch over to when they come under attack then they sell the always on web-based protection to their customers. That’s a pretty common scenario. The nice thing too, this gets back to the how much can you charge. Our service actually offers not just DDoS but also web site protection and acceleration. You’re offering more than just, you’re effectively offering more than just DDoS. You’re offering a whole package which is entirely valued by customers. It’s not on here. I should mention that my email address is just tim@incapsula.com if you prefer email to social media. Nicole: We’ve got another question here, suppose I run a DNS service. How can normal traffic be differentiated from attack traffic since they could look identical? Tim: We distinguish normal from attack based on some of our bot detection capabilities that I mentioned early in the presentation. We’ve got a very deep set of capabilities and they properly identify bots versus humans. That’s how we separate DDoS traffic from legitimate human traffic. If you go to Incapsula.com in our blog, we’ve got a couple of very detailed blog posts about how we distinguish human versus bots, and even stuff about how we distinguish between legitimate Googlebots and bogus bots that are trying to mount DDoS attacks or other attacks. 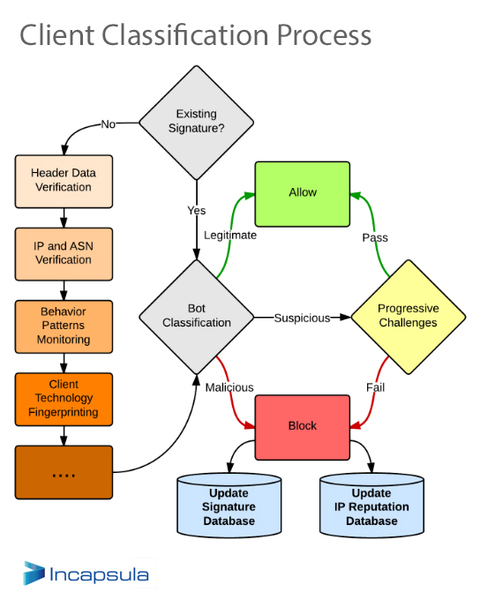 Nicole: The next questions is, I’m currently working with Akamai as my CDN partner, can you coexist? Tim: Yes. We have several customers of ours who are happy with Akamai CDN capabilities and simply want us for DDoS. We do this all the time. Nicole: The last question I’ve got here is, how do I integrate with Incapsula? Do you have an API cPanel? Tim: Yes, we have both. We have an API. We offer a cPanel plug-in. Either one of those is fine. There is documentation on both on the Incapsula.com website. You can go check it out yourself. Nicole: How often do you see attacks directed at Incapsula specifically as opposed to your customers? Tim: I don’t think that we have any attacks that target Incapsula directly, as we are never really the real target. Having said that, as part of our DDoS protection solution we do offer IP masking services, which help prevent direct-to-IP attacks against our clients by having these attacks target our IPs and our network instead. To say this another way, I’ll give you a little bit of the history of the company. The original idea was to set up a web protection offering, just looking to protect web apps from things like SQL injection attacks and other types of web attacks. Early on we realized that there were going to be two problems with that. One was going to be latency, which is why we built the CDN. The other was going to be that we would need to cope with DDoS attacks, which were meant for our clients. We contemplated that scenario from day one and created a massive network to make our service DDoS-resilient. This is actually how our DDoS Protection services were born. Today these DDoS attacks are a non-issue, because not only are we covered ourselves, but we are in the business of protecting others from DDoS attacks. (This answer was amended for accuracy.) Tags: ddos, security, access control, cloud via Incapsula Blog By Tim Matthews / See source above Liquid Layer Networks | Performance Cloud Web Hosting http://www.LiquidLayer.net ParagonHost Networks | Hosting Since 2000 http://www.ParagonHost.net |
||
| Post 1 • IP flag post | ||
Pages:
1
