Cryptolocker: How to avoid ransom malware738
Pages:
1

|
LiquidLayer private msg quote post Address this user | |
| Full blog post on Computer World By Jonathan Hassell FOLLOW Computerworld | Oct 25, 2013 2:45 PM PT  Cryptolocker: How to avoid getting infected and what to do if you are... There's a big threat wiling around on the Internet right now: A particularly nasty piece of ransomware called Cryptolocker. Many, many organizations are being infected with this malware, but fortunately, there are surefire ways to avoid it and also ways to mitigate the damage without letting the lowlifes win. What is Cryptolocker? Cryptolocker comes in the door through social engineering. Usually the virus payload hides in an attachment to a phishing message, one purporting to be from a business copier like Xerox that is delivering a PDF of a scanned image, from a major delivery service like UPS orFedEx offering tracking information or from a bank letter confirming a wire or money transfer. 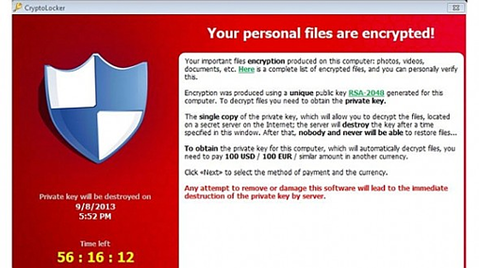 The virus is, of course, an executable attachment, but interestingly the icon representing the executable is a PDF file. With Windows' hidden extensions feature, the sender simply adds ".pdf" to the end of the file (Windows hides the .exe) and the unwitting user is fooled into thinking the attachment is a harmless PDF file from a trusted sender. It is, of course, anything but harmless. Once Cryptolocker is in the door, it targets files with the following extensions: *.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm, *.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx, *.pptm, *.mdb, *.accdb, *.pst, *.dwg, *.dxf, *.dxg, *.wpd, *.rtf, *.wb2, *.mdf, *.dbf, *.psd, *.pdd, *.pdf, *.eps, *.ai, *.indd, *.cdr, *.jpg, *.jpe, img_*.jpg, *.dng, *.3fr, *.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2, *.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem, *.pfx, *.p12, *.p7b, *.p7c When it finds a file matching that extension, it encrypts the file using a public key and then makes a record of the file in the Windows registry under HKEY_CURRENT_USERSoftwareCryptoLockerFiles. It then prompts the user that his or her files have been encrypted and that he or she must use prepaid cards or Bitcoin to send hundreds of dollars to the author of the malware. Once the payment has been made, the decryption usually begins. There is typically a four-day time limit on the payment option; the malware's author claims the private key required to decrypt files will be deleted if the ransom is not received in time. If the private key is deleted, your files will essentially never be able to be decrypted -- you could attempt to brute force the key, but as a practical matter, that would take on the order or thousands of years. Effectively, your files are gone. Currently, the only versions of Cryptolocker in existence target files and folders on local drives and mapped drives. The malware does not currently attempt to perform its malfeasance over network-based universal naming convention paths, although one would surmise this would be a relatively simple change for the author of the ransomware to make. Antivirus and anti-malware programs, either running on endpoints or performing inbound email message hygiene, have a particularly difficult time stopping this infection. Unless you have a blanket email filtering rule stripping out executable attachments, and that tool is intelligent enough to do so without allowing the user to request the item's return from quarantine, you will see your users getting these phishing messages attempting to introduce Cryptolocker. It is only a matter of time. Prevention: Software Restriction Policies and AppLocker As of now, the best tool to use to prevent a Cryptolocker infection in the first place -- since your options for remediating the infection involve time, money, data loss or all three -- is a software restriction policy. There are two kinds: Regular software restriction policies, and then enhanced AppLocker policies. I'll cover how to use both to prevent Cryptolocker infections. Software Restriction Policies Software Restriction Policies (SRPs) allow you to control or prevent the execution of certain programs through the use of Group Policy. You can use SRPs to block executable files from running in the specific user-space areas that Cryptolocker uses to launch itself in the first place. The best place to do this is through Group Policy, although if you're a savvy home user or a smaller business without a domain, you can launch the Local Security Policy tool and do the same thing. One tip: if you're using Group Policy, create a new GPO for each restriction policy. This makes it easier to disable a policy that might be overly restrictive. Learn about GPO Enforcement and the full blog post: Full blog post on Computer World _______________________________________________________ Business Grade Web Hosting for the cost of Starbucks Coffee Liquid Layer Networks | Performance Cloud Web Hosting http://www.LiquidLayer.net |
||
| Post 1 • IP flag post | ||

|
LiquidLayer private msg quote post Address this user | |
| Also another CryptoLocker Prevention Tool ... Both Free and Paid versions: https://www.foolishit.com/cryptoprevent-malware-prevention/ YES, this is the original CryptoLocker prevention tool you’ve read about! CryptoPrevent has been featured on The Today Show, CNBC, Brian Krebs security blog (among many others) and by educators everywhere such as Kim Komando, Ken Dwight ‘The Virus Doctor’, and the infamous Britec (Britec09 on Youtube) to name just a few! CryptoPrevent is an Anti-Virus/Security Software Supplement, originally designed to prevent infection from the CryptoLocker threat which emerged in late 2013. Since that time, CryptoPrevent has grown into a robust solution, providing protection against a wide range of ransomware and other malware. CryptoPrevent doesn’t stop there. We are continuing development efforts to expand the software into something more than just a ‘security’ solution. This is why we would also like to welcome recent additions to the CryptoPrevent research and development team! We look forward to seeing the results of their efforts in the second half of the year! CryptoPrevent supports any Windows version (XP, Vista, 7, 8, 8.1, and 10 – including Windows ‘Home’ editions) Month-long Descending Sale! Current savings of 25% off CryptoPrevent Editions using the coupon code: foolishworld Month-long Descending Sale! Current savings of 25% off CryptoPrevent Editions using the coupon code: foolishworld CryptoPrevent version 8 is coming soon! (Available through Premium automatic updates!) The current ‘One-time Purchase’ option will expire soon! Individual sales of CryptoPrevent Premium Edition as a ‘One-time Purchase’ option will be retired after the next major release (v8.0) which is fast approaching. It will be replaced by a new edition with a low cost annual subscription rate, and include some exciting new features not available to the current Premium Edition. While the Premium Edition will no longer be sold by Foolish IT however, 3rd party distributors (such as a reputable local PC Repair Shop) may continue to resell the Premium Edition independently as licensed by Foolish IT. Customers of the existing Premium Edition will continue to enjoy all of the benefits and features they are used to, with additional benefit from the continued software updates provided by our new development team. Finally, users of the Free Edition will continue to enjoy the same comprehensive protections of the newer releases, from which ALL editions benefit. We strongly believe that our ever-improving malware prevention features, which are a vital complement to existing anti-virus software protection, should remain FREE to all who desire an extra layer of security. |
||
| Post 2 • IP flag post | ||

|
LiquidLayer private msg quote post Address this user | |
| From Krebs on Security http://krebsonsecurity.com/2013/11/how-to-avoid-cryptolocker-ransomware/ Over the past several weeks, a handful of frantic Microsoft Windows users have written in to ask what they might do to recover from PC infections from “CryptoLocker,” the generic name for an increasingly prevalent and nasty strain of malicious software that encrypts your files until you pay a ransom. Unfortunately, the answer for these folks is usually either to pay up or suck it up. This post offers a few pointers to help readers avoid becoming the next victim. A Cryptolocker prompt and countdown clock. Photo: Malwarebytes.org A CryptoLocker prompt and countdown clock. Image: Malwarebytes.org According to reports from security firms, CryptoLocker is most often spread through booby-trapped email attachments, but the malware also can be deployed by hacked and malicious Web sites by exploiting outdated browser plugins. The trouble with CryptoLocker is not so much in removing the malware — that process appears to be surprisingly trivial in most cases. The real bummer is that all of your important files — pictures, documents, movies, MP3s — will remain scrambled with virtually unbreakable encryption unless and until you pay the ransom demand, which can range from $100 to $300 (and payable only in Bitcoins). File-encrypting malware is hardly new. This sort of diabolical threat has been around in various incarnations for years, but it seems to have intensified in recent months. For years, security experts have emphasized the importance of backing up one’s files as a hedge against disaster in the wake of a malware infestation. Unfortunately, if your backup drives are connected physically or via the local network to the PC that gets infected with CryptoLocker, your backups may also be encrypted as well. Computers infected with CryptoLocker may initially show no outward signs of infection; this is because it often takes many hours for the malware to encrypt all of the files on the victim’s PC and attached or networked drives. When that process is complete, however, the malware will display a pop-up message similar to the one pictured above, complete with a countdown timer that gives victims a short window of time in which to decide whether to pay the ransom or lose access to the files forever. Fortunately, there are a couple of simple and free tools that system administrators and regular home users can use to minimize the threat from CryptoLocker malware. A team of coders and administrators from enterprise consulting firm thirdtier.net have released the CryptoLocker Prevention Kit — a comprehensive set of group policies that can be used to block CryptoLocker infections across a domain. The set of instructions that accompanies this free toolkit is comprehensive and well documented, and the group policies appear to be quite effective. Read the reaming content of the blog post on Krebs: http://krebsonsecurity.com/2013/11/how-to-avoid-cryptolocker-ransomware/ |
||
| Post 3 • IP flag post | ||
Pages:
1
